Analytics technology has become fundamental to many aspects of organizational management. Some of the benefits of analytics actually have crossover with each other.
For example, more companies than ever are using analytics to bolster their security. They are also using data analytics tools to help streamline many logistical processes and make sure supply chains operate more efficiently. These companies have since realized that analytics can be invaluable to helping improve the security of supply chain systems.
The market for security analytics will be worth over $25 billion by 2026. You can learn more about the benefits by reading below.
Analytics is Making the Security of Supply Chains Far More Robust
Supply chain refers to the ecosystem of resources used in designing, manufacturing, and distributing a product. For example, hardware and software, the cloud and local storage, and delivery systems are components of the cybersecurity supply chain. Supply chain analytics also plays a huge role.
Every organization requires various third-party services and software to carry out its daily operations. Many of these third-party organizations offer invaluable analytics capabilities, which can help address countless logistical issues. This means that the organization must rely on other organizations for many things, such as third-party chat applications, to interact internally. The supply chain is referred to because many items are procured from outside sources.
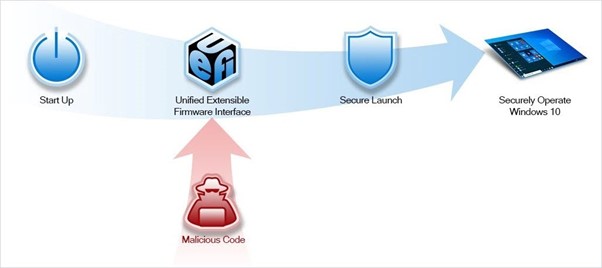
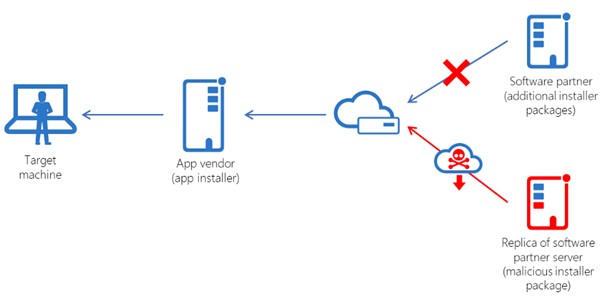
Supply chain attacks are typically concerned with cyber security, and a single attack on a single supplier might compromise a large number of organizations, for example, by spreading malware throughout the supply chain.
Analytics technology can help identify some of the security threats that businesses are encountering. A number of tools merge AI and analytics algorithms to improve their threat scoring challenges and engage in automated prevention measures as hackers try to orchestrate these attacks. This is leading to a new era of security analytics.
Supply Chain Security with Analytics Capabilities
Software supply chain security is primarily concerned with securing your process to ensure you can provide customers with what they require at the most fortuitous timing and price and with adequate protection. Any disruptions and risks to the integrity of the delivered products or services compromise the organization’s privacy and its data. So, you must implement a wide range of cyber security practices for trust to be easily established and for your organization to operate efficiently.
You will be able to address these threats more easily with the right analytics-based cybersecurity strategy in place. However, you must first educate yourself about the different cybersecurity threats and analytics tools that can help prevent them.
Organizations must adhere to the following analytics-driven tactics and procedures to reduce the risks associated with the supply chain.
Performing Vendor Review
Every organization should conduct a vendor review of the third-party service provider before implementing any software in their organization. This provides essential clarity regarding the software supply chain security of that vendor.
The vendor review should include an evaluation of how the data is handled by the vendor and what data protection methods are in operation on the vendor’s premises. This provides a clear image of the third-party provider and their rules, allowing businesses to make more informed decisions about whether or not they should include the software in their operations.
Analytics technology can make it easier to learn more about different vendors. There are a lot of data mining tools that can analyze ratings on different vendor review sites, which can help you more quickly identify the best candidates to handle the job.
Performing Vulnerability Assessment
To be considered complete, the vulnerability assessment should be done on all devices that are part of the infrastructure. These can be performed on both new and old apps to ensure that the applications are secure and that the individuals in charge are doing an excellent job of administering them. Organizations can also enlist the assistance of a purple or red team simulation to assess the level of cyber security knowledge among their workforce.
Analytics technology has become a lot more important with vulnerability assessments. You will be able to use analytics tools to evaluate the security architecture of your cybersecurity defense system and come up with actionable strategies to address concerns.
Modernization and Digitization
There are a few things that we cannot digitize. For example, if the business is still reliant on paper, monitoring access control and security will be challenging to manage because they are generated by third-party processes. It is recommended that instead of making physical copies, you utilize the digital version to prevent the exposure of sensitive information. Digitalization also facilitates access control for both the products and the data.
Encryption
To mitigate the risks resulting from supply chain attacks, it is necessary that any data that contains critical information about customers be encrypted at all times. Therefore, customer data will be protected in a malware attack. Additionally, all sensitive data that can be accessed by third-party systems should be protected using encryption or different authentication factors.
Analytics is Essential for Improving Supply Chain Security
Attacks on the supply chain are now causing worry because every organization relies on third-party vendors to maintain its day-to-day operations. The good news is that analytics technology is becoming very useful in thwarting these problems. However, threat attackers are now focusing their attention on the vendors as it allows them to infect a large number of companies. As a result, it is critical to implement controls and conduct regular reviews to ensure that the organization is not adversely affected if any vulnerability in a supply chain is exploited.