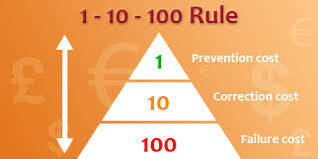
Why Data Should Be a Business Asset: The 1-10-100 Rule
If you run a business, or even just run a household, you’ll understand that chaos creates waste. How many times…
IDE and Debugging Function Comparison Between esProc, Perl and Python
esProc, Perl, and Python are all the scripting language for data analysis and processing. However, they differ in syntax style,…
Businesses Must Make Self-Service Reporting a Priority
One of the charitable causes to which I devote time puts on an annual vintage car show. The Concours d’Élegance…
The Next Generation of Predictive Analytics
Our benchmark research consistently shows that business analytics is the most significant technology trend in business today and acquiring effective…
Data Breach Reporting: A Job Killer or Business Saver?
There’s quite a brouhaha bubbling up Down Under.It all stems from a Sydney Morning Herald opinion piece written by the…
How to Create an OBIEE Dashboard Tutorial
This OBIEE training tutorial will show you the basic steps required to build an Oracle OBIEE dashboard. By building on…
Why Oh Why Is It So Difficult? Implementing Sales and Operations Planning
Sometimes the hardest part about implementing Sales and Operations Planning (or any project) is just getting started. Sometimes the hardest…
Assisted Insight: The Future of Data Discovery
Businesses don’t want "data discovery", "visualization" or "analytics" tools – businesses want one thing: insight.The challenge has been how to provide…
How to Address the Big Data Talent Challenge
One of the greatest Big Data challenges ahead of us is the scarcity in the available talent. One of the…
Where in the World Does All this ESRI World Data Come from?
I was left highly impressed, and still deeply curious, about the guts behind what I saw attending the ESRI User…