Secure Socket Layer, or SSL for short, is one of the key elements to providing a safe and secure web transaction. Websites that offer financial services or handle confidential user information have for long used SSL technology to encrypt such sensitive data and thus deter hackers from stealing them.
Secure Socket Layer, or SSL for short, is one of the key elements to providing a safe and secure web transaction. Websites that offer financial services or handle confidential user information have for long used SSL technology to encrypt such sensitive data and thus deter hackers from stealing them.
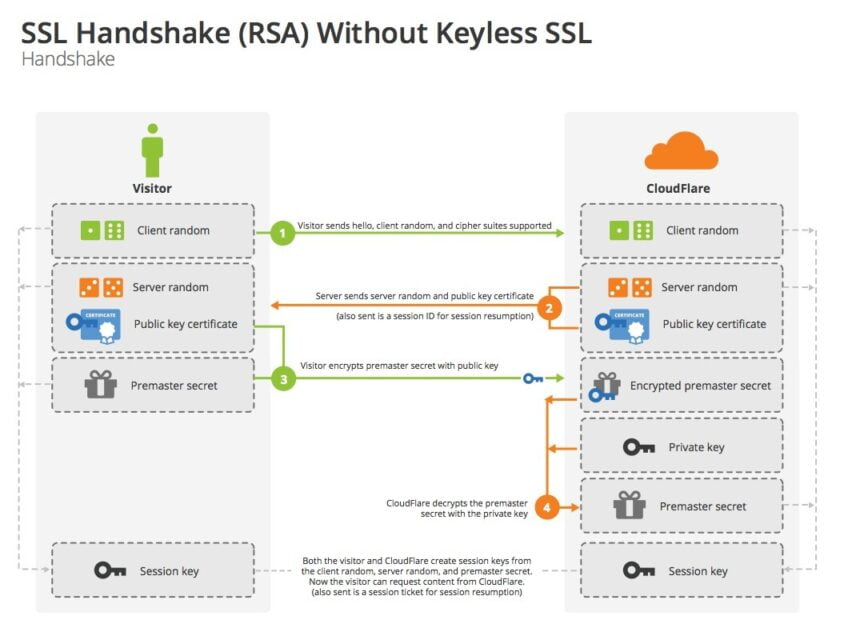
Typically, SSL deployment happens with the help of a public key-private key pair. When a browser requests access to a secure page (https in most cases), it first receives a public key from the web server that is used by the browser to encrypt a random symmetric encryption key. This process is called the encryption handshake. This is then sent to the server along with other required data (which is also encrypted).
Once the server receives this information, it decrypts the data using a private key and processes the information. The output is now passed on to the browser with the help of the random symmetric encryption key. This is now decrypted by the browser before being displayed to the user. The complete process of how this happens is provided in the visual below:
 Recently however, CloudFlare has come up with an alternate SSL technology that does not require the traditional handshaking process. In this article, we will take a look at how this technology works and compares with the traditional SSL protocol. But in case you didn’t know what CloudFlare does, here is a brief : CloudFlare is a content delivery network (CDN) that protects websites from sudden traffic surges and potential DDoS (Distributed Denial of Service) attacks. This is achieved through the use of their virtualized servers that are spread across the internet. Here is a video that demonstrates what they do (Courtesy : Arvixe Web Hosting)
Recently however, CloudFlare has come up with an alternate SSL technology that does not require the traditional handshaking process. In this article, we will take a look at how this technology works and compares with the traditional SSL protocol. But in case you didn’t know what CloudFlare does, here is a brief : CloudFlare is a content delivery network (CDN) that protects websites from sudden traffic surges and potential DDoS (Distributed Denial of Service) attacks. This is achieved through the use of their virtualized servers that are spread across the internet. Here is a video that demonstrates what they do (Courtesy : Arvixe Web Hosting)
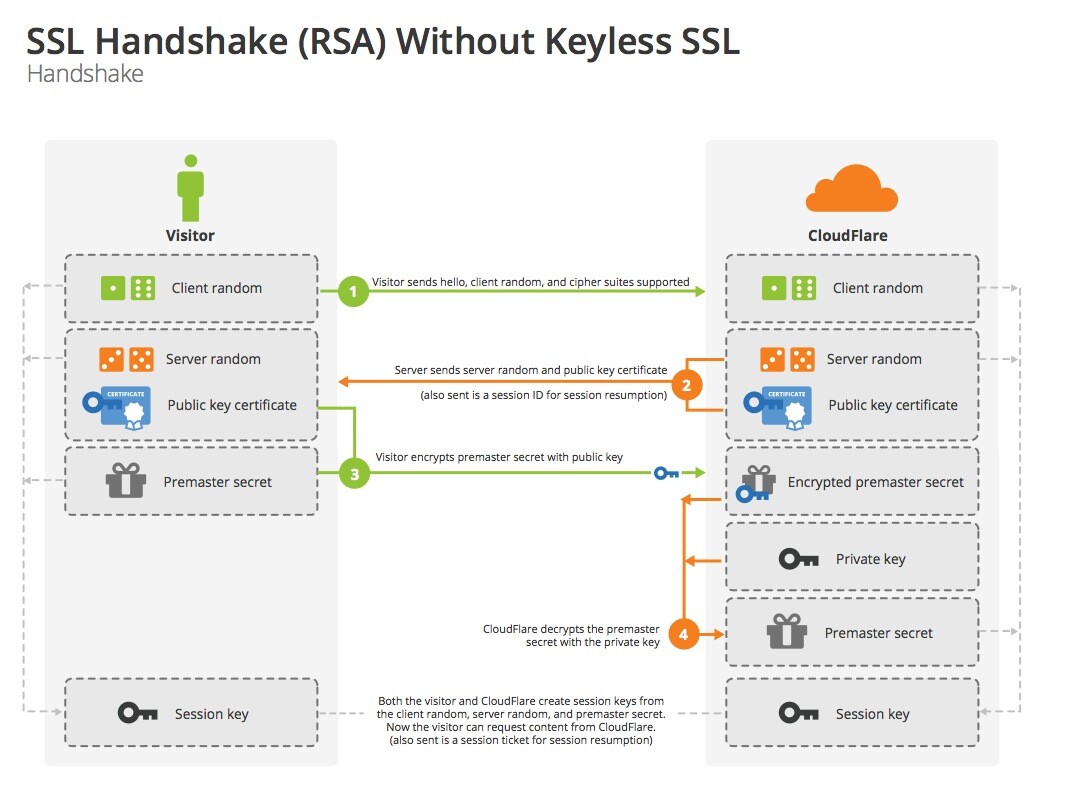
In keyless SSL used by CloudFlare, the “handshake” operations are typically broken down into two segments. One, the public key operation, and Two, the private key operation. In order to prevent the private key from being handed over to a third party, all aspects of the private key handshaking process happens within the origin website’s infrastructure. To do this, CloudFlare simply sets up a remote key server at the customer’s end. This way, the private part of the handshaking process is complete within the origin web server and thus stays exclusive.
So what happens now is that when a visitor approaches a secure website, the web server first sends out the public key certificate along with the random symmetric encryption key to the browser. At the same time, it passes along the information to the remote key server for signing the public key certificate along with the client and server randoms. This is responded to by the key server once the private key data has been authenticated. Once complete, CloudFlare goes ahead with the rest of the process required to output content to the user. Here is a visual representation of how the keyless SSL works
![]()
So as you can see, keyless SSL does not technically do away with the public key-private key pairs. Instead it has tweaked the Transport Security Layer (TLS) process in a way that is harder to break into.