Data breaches can happen at multiple levels. Among a recent surge of data breaches, the ones with the greatest publicity are usually those affecting prominent websites or online services, as shown by the recent data breach scandals affecting Facebook and Dropbox. The record for the greatest data breach in history seems to be held by Yahoo – in 2013-2014, about three billion accounts were affected. In this particular case, securing user-related information is a responsibility of the respective online platforms. Users cannot take many additional precautions other than to be cautious about the information they share or store using these platforms. Smaller data breaches can involve local ISPs, proxy servers, or even user’s home networks or Internet devices. These can be equally catastrophic, especially when financial information is involved (e.g. credit card details, online banking login credentials). 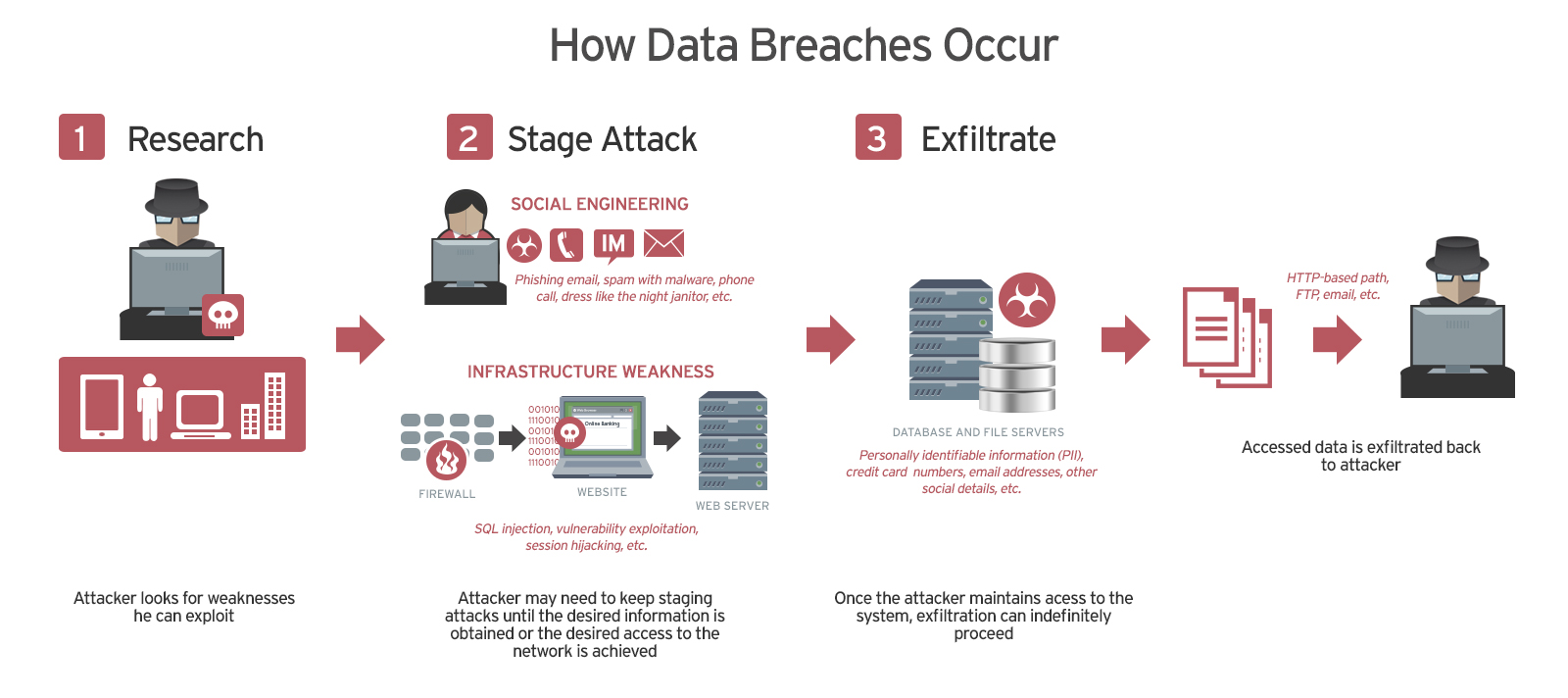
- your physical IP address,
- your country,
- your Internet Service Provider,
- the hostname,
- the operating system,
- the browser you use (including the version).
A lot more information can be obtained about you based on your online activity. In fact, even such apparently mundane data such as the size of your monitor (in pixels) or your operating system can be used to track your footprints on the web.
The Misconceptions About Incognito Mode
Many browsers do offer the equivalent of the Incognito Mode present in Google Chrome. Although the names vary, the functioning principle is basically the same – the entire activity during Incognito sessions is not recorded in the local browsing history. After the session is terminated, created cookies are deleted (cookies are small text files created on the user’s device by websites and subsequently used by these to identify the user whenever he/she accesses the website). As argued on this site, users often tend to misinterpret the functions of the Incognito mode, whose primary role is to only hide their browsing activity so that other users of the same device or account do not see it. However, when it comes to securing their online activity or hide their identity from the ISP, hackers, government, etc., Incognito Mode fails miserably.
VPNs As The Solution For Securing User Data And Online Activity
At first glance, it seems that users find it hard to achieve personal security using common tools. Fortunately, this is not true at all, with some very elegant solution being developed for both businesses and average users. While safe browsing itself can be achieved by using the TOR browser (it is notoriously slow but nevertheless, reliable), Virtual Private Networks (VPNs) are the true comprehensive answer to online security. The key reason is that VPNs create secure communication channels in which all the data traffic occurring between the user and the Internet is encrypted. This makes it incredibly more difficult to eavesdrop on your data traffic, even for the ISP (obviously, it applies to other parties on the net). In addition, VPN providers route the data traffic through their own servers before connecting you to the Internet, creating an additional layer of security because any attack directed at you would actually hit the server in the very first place (which, obviously, has better security tools than the average user). The implications of all these for protecting both your data traffic and your stored data are huge because anything you do online from this point on is permanently hidden from anyone. This protection can be extended to all the devices used by you given that many VPNs offer protection for multiple devices but also work with WiFi routers to help secure entire networks, thus, eliminating any vulnerable links in your house (e.g. TV boxes, Internet of Things devices, etc.). In case you’d like to delve deeper into the topic, there are several good resources on the web to start with. This resource not only helps you understand and assimilate the basic concepts about VPNs, but also helps you decide which features to focus on given your individual needs – for instance, if security is a priority (as compared to Internet speed and access to geographically restricted content), you would probably be tempted to choose a VPN service with a stronger encryption key, no logs policy, or additional security features (such as a “kill switch”). Based on the selected priority features, you can proceed exploring and comparing the most popular VPN service providers listed, so that you can choose one that suits you.
Big Data Has Led to a Surge in Data Breaches. Stay Protected!
Big data is a double-edged sword for customers. It provides many benefits. But it can be a serious problem if your data is compromised. Make sure that you take all reasonable steps to protect your data from hackers.